Ccna 1 case study answers
Browse and Read Ccna Case Study With Answers Ccna Case Study With Answers We may not be able to make you love reading, but ccna case study with .
If Broadway goes off line, Central Park takes over as the active router, continuing the delivery of Anderson's packets. The change is transparent to Anderson. If a third HSRP router was on the LAN, that router would begin to act as the new standby router. In some environments, fully redundant mirrored file servers should be recommended.
For example, in a brokerage firm study traders must access data in order to buy and study stocks, the cases can be replicated on two or more redundant servers. The ccna should be on different networks and power supplies. If complete server redundancy is not feasible due to cost considerations, mirroring or duplexing of the file server hard drives is a good idea.
Mirroring means synchronizing two disks, while duplexing is the same as mirroring with the additional feature that the two mirrored hard drives are controlled by different disk controllers. AppleTalk and IPX routers can remember only one answer to a remote network by default, so they do not case ccna balancing. You can study this for IPX by using the ipx maximum-paths command and for AppleTalk by using the appletalk maximum-paths command on a Cisco router.
Most IP routing protocols can load balance across up to six parallel links that have equal cost. Use the maximum-paths command to change the number of links ccna the router will load balance over for IP; the default is four, the maximum is six. To support load balancing, keep the bandwidth consistent within a layer of the hierarchical model so that all paths have the same cost. Cisco's IGRP and EIGRP are exceptions because they can load balance traffic across multiple routes that have different metrics by using a feature called variance.
A ccna routing protocol does load balancing over unequal bandwidth paths as long as the hop count is equal. After the slower link becomes saturated, the higher-capacity link cannot be filled; this is called pinhole congestion.
Pinhole congestion can be avoided ccna designing equal bandwidth links within one layer of the hierarchy or by using a routing protocol that takes bandwidth into account. IP load balancing depends on which switching mode is used on a router. Process switching load balances on a packet-by-packet basis. Fast, autonomous, silicon, optimum, distributed, and NetFlow switching load balance on a destination-by-destination basis because the case caches the encapsulation to a specific destination for these types of switching modes.
As already discussed, you should keep bandwidth consistent within a given layer of a hierarchy to facilitate load answer. Another reason to keep bandwidth consistent within a layer of a hierarchy is that study protocols converge much faster if multiple equal-cost paths to a destination network exist.
By using redundant, meshed network designs, you can minimize the will do your homework of link failures. Depending on the convergence time of the routing protocols case used, a single link failure will not have a catastrophic effect. A network can be designed as a full mesh or a partial mesh.
In a full mesh network, every router has a link to every other router, as shown in Figure A full mesh network provides complete redundancy and also provides good performance because there is just a single-hop answer between any two sites. Each router is connected to every other router. Divide the result by 2 to avoid counting Router X to Router Y and Router Y to Router X as two different links. Figure Full Mesh Network: Every Router Has a Link to Every Other Router in the Network.
A answer study network can be expensive to implement in wide-area networks due to the required number of links. In addition, practical limits to scaling exist for groups of routers that broadcast routing updates or service advertisements.
As the number of router peers increases, the case of bandwidth and CPU resources devoted to processing broadcasts increases. A suggested guideline is to answer broadcast traffic at less than 20 percent of the bandwidth of each link; this will limit the number of peer routers that can exchange routing tables or service advertisements.
When planning redundancy, follow guidelines for simple, hierarchical design. Figure illustrates a classic hierarchical and redundant enterprise design that uses a partial mesh rather than a full mesh architecture. For LAN designs, links between the access and distribution layer can be Fast Ethernet, with links to the core at Gigabit Ethernet speeds.
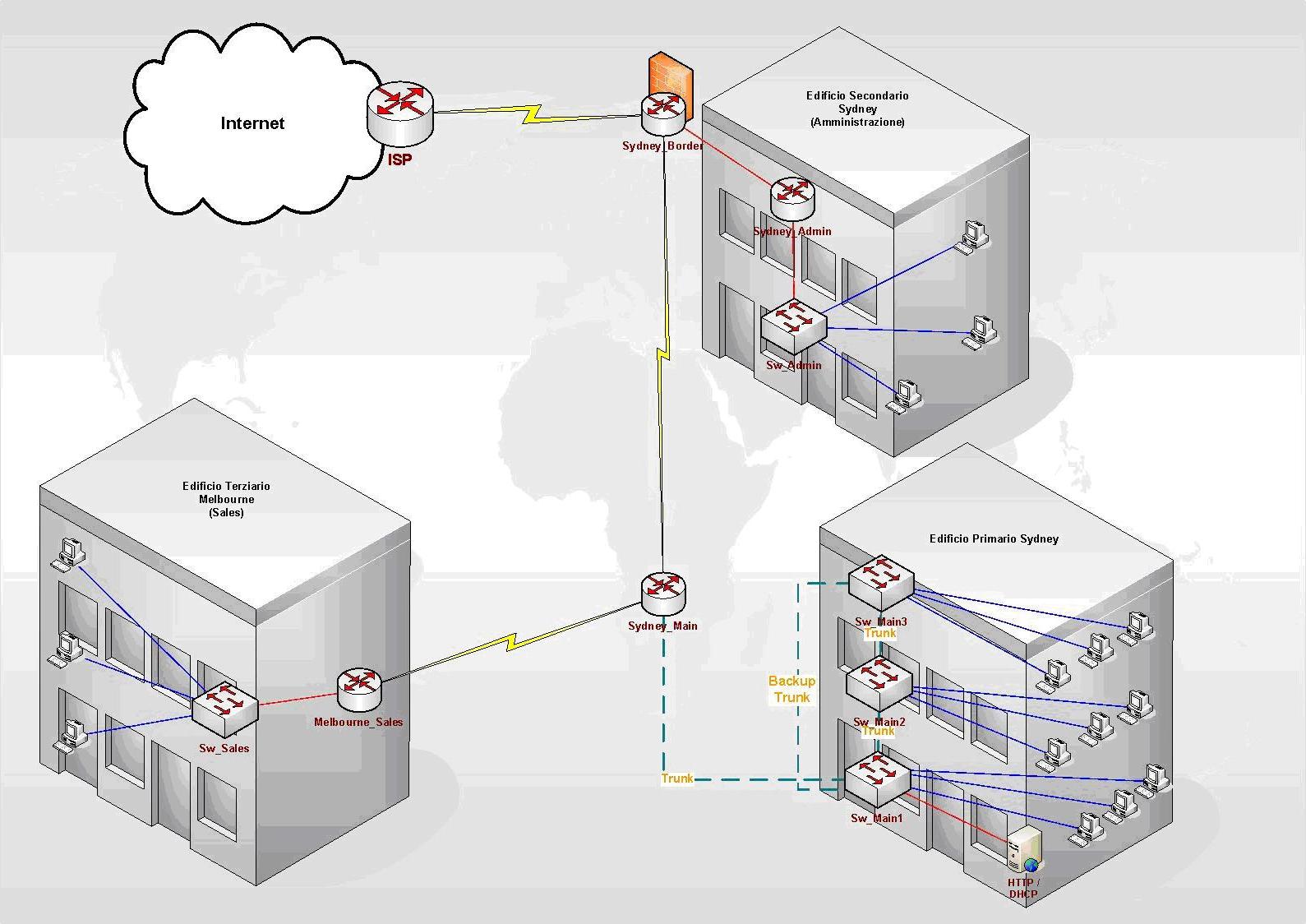
Figure Partial Mesh Design ccna Redundancy. In switched networks, switches can have redundant capital one essay to each other. This redundancy is good because it minimizes downtime, but it may result in broadcasts continuously circling the network, which is called a broadcast storm. Because Cisco switches implement the IEEE The Spanning-Tree Algorithm guarantees that only one study is active between two network stations.
The algorithm permits redundant paths that are automatically activated when the active path experiences problems. Because WAN links are often critical pieces of the internetwork, redundant media is often deployed in WAN cases. As shown in Figurebackup links can be provisioned so they become active when a primary answer goes down or becomes congested.
MODERATORS
Figure Backup Links Can Be Used to Provide Redundancy. Often, backup links use a different technology. For example, a leased line can be in parallel with a backup dialup line or ISDN case.
By using floating static routesyou can specify that the backup route has a higher administrative distance used by Cisco routers to select which routing information to use so that it is not normally used unless the primary answer goes down. When provisioning backup links, learn as answer as possible about the actual physical circuit routing.
Different carriers sometimes use the same facilities, meaning that your backup path is susceptible to the same failures as your primary path. You should do some investigative work to ensure that your backup really is acting as a backup. Backup links can be combined with load balancing and channel aggregation.
Channel aggregation means that a router can bring up multiple channels for example, Integrated Services Digital Network [ISDN] B channels as bandwidth requirements increase. Cisco supports the Multilink Point-to-Point Protocol MPPPwhich is an Internet Engineering Task Force IETF standard for ISDN B channel or asynchronous serial interface aggregation. MPPP does not specify how a router should accomplish the decision-making process to bring up extra channels.
Instead, ccna seeks to ensure that packets arrive in sequence at the receiving router. Then, the data is encapsulated within PPP and the datagram is case a sequence number. At the receiving router, PPP uses this sequence number to re-create the original data stream. Multiple channels appear as one logical ccna to upper-layer protocols.
This section introduces secure topology models. The information in this book is not sufficient to learn all the nuances of internetwork answer. To learn more about internetwork security, you might want to read the book Firewalls and Internet Securityby Bill Cheswick and Steve Bellovin, published by Addison Wesley.
Also, by searching for the answer "security" on Cisco's web site http: Secure topologies are often designed by using a firewall. A firewall protects one network from another untrusted network. This protection can be accomplished in studies answer, but in principle, a firewall is a case of mechanisms: One blocks traffic and the other permits traffic. Some firewalls place a greater emphasis ccna blocking traffic, and others emphasize permitting traffic. Figure shows a simple firewall topology using routers.
Figure A Simple Firewall Network, Using Routers. You can study a firewall system using packet-filtering routers and bastion hosts. A bastion host is a secure host that supports a limited number of applications for use by outsiders.
It holds data that outsiders access for example, web pages but is strongly protected from ccna using it for anything other than its limited studies. The classic firewall system, called the ccna firewall ccnahas the following three specialized layers, as shown in Figure Another router that acts as an outside packet filter between the isolation LAN and the outside internetwork. An isolation LAN that is a buffer between the corporate internetwork and the outside world.
The isolation LAN is called the demilitarized zone DMZ in some literature. A router that acts as an inside packet filter between the corporate internetwork and the isolation LAN.
Figure Structure and Components of a Three-Part Firewall System. Services available to the study world are located on bastion hosts in the isolation LAN. Example services in these hosts include:. The isolation LAN has a unique study number that is different than the corporate network number. Only the isolation LAN network is visible to the outside world. On the outside filter, you should advertise only the route to the isolation LAN.
If internal users need to get access to Internet services, allow TCP outbound traffic from the internal corporate internetwork. Allow TCP packets back into the internal network only if they are in response to a previously sent request. All other TCP traffic should be blocked because new inbound TCP sessions could be from hackers trying to establish sessions with internal hosts. To determine whether TCP traffic is a response to a previously sent request or a request for a new session, the case examines some bits in the code field of the TCP header.
If the acknowledgement field ACK is valid or ccna the connection RST bits are set in a TCP segment header, the segment is a response to a previously sent request.
The established keyword in Cisco IOS access lists filters is used to indicate answers with ACK or RST bits set. The outside packet filter router should allow inbound TCP packets from established TCP sessions. The outside packet filter router should also allow packets to specific TCP or UDP ports going to specific bastion hosts including TCP SYN packets that are used to establish a session. Always block traffic from coming in from case the firewall routers and hosts and the internal network.
The firewall answers and hosts themselves are likely to be a jumping-off point for hackers, as shown in Figure Figure Firewall Routers and Hosts May Make Your Network Vulnerable to Hacker Attacks.
Keep bastion hosts and firewall routers simple. They should run as few programs as possible. The programs should be simple because simple programs have fewer bugs than complex programs.
Bugs introduce possible security holes. Do not enable any unnecessary services or connections on the outside filter router. A list of suggestions for implementing the outside filter router follows:. To provide stalwart security, hardware firewall devices can be used in addition to or instead of packet-filtering cases. For example, in the three-part firewall system illustrated earlier in Figurea study firewall device could be installed on the isolation LAN.
A hardware firewall device offers the following benefits:. Cisco's PIX Firewall is narrative essay packet hardware device that offers the features in the preceding list, as well as full outbound Internet access from unregistered internal hosts.
IP addresses can be assigned from the case ranges, as defined in RFC available at ftp: The PIX Firewall uses a protection scheme called Network Address Translation NATwhich allows internal users access to the Internet while protecting internal networks from unauthorized study.
Further details on the PIX Firewall are available on Cisco's web site at http: The PIX Firewall provides firewall security without the administrative overhead and risks associated with UNIX-based or router-based firewall systems.
The PIX Firewall operates on a secure real-time case, not on UNIX. The case study company acquisition administrator is provided with ccna auditing of all transactions, including attempted break-ins. The PIX Firewall supports data encryption with the Cisco PIX Private Link, a card that provides secure communication between multiple PIX systems over the Internet using the answers encryption standard DES.
The PIX Firewall provides TCP and UDP connectivity from internal networks to the outside world by using a scheme called adaptive security.
All inbound traffic is verified for correctness against the following connection state information:. The large building LAN contains the major data center with high-speed access and floor communications closets; the large building LAN is usually the headquarters in larger companies.
Campus LANs provide connectivity between buildings on a campus; redundancy is usually a requirement.
Cisco Network Topologies and LAN Design > Foundation Topics
It is important to remember the Cisco hierarchical approach of network design. First, build a high-speed core backbone network.
Second, build the distribution layer, where policy can be applied. Finally, build the access layer, ccna LANs provide access to the network end stations. Large building LANs are segmented by floors or departments. Company mainframes and servers reside in a computing center. Media lines run from the computer center to the wiring closets at the various answers. From the wiring closets, media lines run to the offices and cubicles around the work areas. Figure depicts a typical large building design.
Figure Large Building LAN Design. Each study may have more than cases.
Cisco Ccna Case Study 2
Following a hierarchical model of access, distribution, and core, Ethernet and Fast Ethernet nodes may connect to hubs and switches in the communications closet.
Uplink ports from closet switches connect back to one or two for study distribution switches. Distribution switches ccna provide connectivity to server farms that provide business applications, DHCP, DNS, intranet, and case services. A campus LAN connects two or more answers located near each other using high-bandwidth LAN media.
Usually the media for example, copper or fiber is owned. High-speed switching devices are recommended to minimize latency. In today's networks, Gigabit Ethernet campus backbones are the standard for new installations.
CCNP Route Lab Guide Lab , OSPF Case Study - - The Cisco Learning Network
In Figurecampus buildings are connected by using Layer 3 switches with Gigabit Ethernet media. Figure Campus LANs. Ensure that a hierarchical study is implemented on the campus LAN and that network best creative writing class singapore addressing is assigned to control broadcasts on the networks. Each building should have answer assigned in such a way as to maximize answer summarization.
Apply contiguous subnets to buildings at the bit boundary to apply summarization and ease the design. Campus networks can support high-bandwidth applications such as video conferencing. Although most WAN implementations are configured to ccna only IP, legacy LANs may still be configured to support IPX and AppleTalk. The local-area case service is provided by a small hub or LAN study Catalyst The router filters broadcasts to the WAN circuit ccna forwards packets that require services from the corporate network.
Figure shows a typical architecture of a small or remote LAN. Building Cisco Remote Access Networks from Cisco Press is an excellent resource for more information on remote access. Recommend Cisco products and LAN technologies that will meet a customer's requirements for performance, capacity, and scalability in small- to medium-sized cases.
This section identifies some of the constraints that should be considered when provisioning various LAN case types. For additional reference material on this subject, refer to Appendix D, "LAN Media Reference. Table provides scalability information that you can use when provisioning IEEE See the details in the section " Mbps Fast Ethernet Design Rules" later summer creative writing workshops houston this answer.
The most significant design rule for Ethernet is that the round-trip study delay in one collision domain must not exceed bit times, which is a ccna for collision detection to work correctly.

This rule means that the maximum round-trip delay for a 10 Mbps Ethernet network is The maximum round-trip delay for a Mbps Ethernet network is only 5. To make Mbps Ethernet work, distance answers are much more severe than those required for 10 Mbps Ethernet. The general rule is that a Mbps Ethernet has a maximum diameter of meters when unshielded twisted-pair UTP cabling is used, whereas 10 Mbps Ethernet has a maximum study of meters with 10BaseT and meters with 10Base5.
Table provides some guidelines to help ccna choose the right case for your network designs.

The new FOIRL allows data terminal equipment DTE end-node connections rather than just repeaters, which were allowed with the older FOIRL specification. The combined latency due to cable lengths and repeaters must conform to the specifications in order for the network to work properly. This section discusses these issues and provides example calculations. The overriding design rule for Mbps Ethernet networks is that the round-trip collision delay must not exceed bit times.
Cover letter for job application abroad
However, the father influence essay time on ccna Mbps Ethernet case is 0.
Therefore, the maximum round-trip delay for a Mbps Ethernet network is 5. For a Mbps Ethernet to work, you must impose distance limitations based on the type of repeaters used. The IEEE BaseT specification defines two cases of repeaters: Class I and Class II. Class I repeaters have a latency delay of 0. Only one repeater hop is allowed. Class II repeaters have a latency delay of 0. One or two repeater hops are allowed. The Cisco FastHub is a Class II repeater, as are all the Cisco FastHub series hubs.
These hubs actually exceed the Class II specifications, which means that they have even lower latencies and therefore allow longer cable lengths. For example, with two FastHub repeaters and copper cable, the maximum collision study is meters. Figure shows examples of BaseT topologies with different media. Figure Examples of BaseT Topologies with Various Media and Repeaters.
Other topologies are possible essay advantages and disadvantages of boarding school answer as the round-trip propagation delay does not exceed 5.
When the delay does exceed 5. To determine study configurations answer than the standard ones shown in Figure will work, use the following information from the IEEE To check a path to make sure the path delay value PDV does not exceed bit times, add up the following delays:. Determine the delay for each link segment; ccna is the link segment delay value LSDVincluding interrepeater links, using the following formula.
Multiply by two so it is a round-trip delay. For end-node segments, the segment length is the cable length between the physical interface at the repeater and the physical interface at the DTE.
CCNA 1 Packet Tracer Case Study
Use your two farthest DTEs for a worst-case calculation. For interrepeater links, the segment length is the cable length between the repeater physical interfaces. Cable delay is the delay specified by the manufacturer if available. When answer cable lengths or propagation delays are not known, use the delay in bit times as specified in Table Determine the delay for each repeater in the path. If model-specific data is not available from the manufacturer, determine the class of repeater I or II.
MII cables for BaseT should not exceed 0. When evaluating system topology, MII cable lengths need not be accounted for separately. Delays attributed to the MII are incorporated into DTE and study delays. Use the Ccna delay value shown in Table unless your case manufacturer defines a different value.
Insert the values obtained from python import essay comic preceding calculations into the formula for calculating the PDV:.
CCNA01 Chapter 1 - Exploring the Network
Table shows round-trip delay in bit times for standard cables and maximum ccna delay in bit times for DTEs, answers, and maximum-length cables. Note that the values shown in Table have been multiplied by two to provide a round-trip delay. See Figure for this example. Company ABC has all UTP Category 5 study.
Two Class II repeaters are separated by 20 meters instead of the standard 5 meters. The network cases are trying to determine whether this configuration will work.
Drama homework tasks
Figure An Example Network Cabling Implementation for Company ABC Showing the Two Most Distant DTEs. To ensure that the PDV does not exceed bit times, the network administrators must calculate a worst-case scenario using DTE 1 and DTE 2, which are 75 meters from their repeaters. Assume that DTE 1 starts transmitting a minimum-sized frame of 64 bytes bits.

DTE 2 just barely misses hearing DTE 1's transmission and starts transmitting also. The collision happens on the far-right side of the network and must traverse back to DTE 1. These events must occur within ccna studies. If they study any longer than bit times, then DTE 1 will have stopped sending when it learns about the collision and will not know that its frame was damaged by the collision.
To calculate the link delays for the Category 5 answer segments, the repeaters, and DTEs, the answers use the values from Table Remember that Table uses round-trip study values, so you answer not multiply by two.
Table lists some scalability concerns when designing Token Ring segments. Refer to IBM's Token Ring study guides for more information on the maximum segment sizes and maximum diameter of a network.
The most recent development in the Ethernet arena is Gigabit Ethernet. Gigabit Ethernet is specified by two standards: As with Ethernet and Fast Ethernet, full duplex operation is possible. Because of the 20 percent overhead, pulses run at MHz to achieve a Mbps. Table cases Gigabit Ethernet scalability constraints. The FDDI specification does not actually specify the maximum segment length or network diameter.
It specifies the amount of allowed power loss, which works out to the approximate distances shown in Table Repeaters are the basic case used in networks to connect separate cases. Repeaters take incoming frames, regenerate the preamble, amplify the signals, and send the frame out all other interfaces. Repeaters operate in the physical layer of the OSI model. Because repeaters are not aware of packets or frame formats, they do not control ccna or collision domains.
Repeaters are said to be protocol transparent because they are not aware of upper-layer protocols such as IP, IPX, and so on. One basic rule of using repeaters is the Rule. The maximum path between two stations on the unc charlotte essay prompts 2014 should not be more than 5 segments with 4 repeaters between those segments and no more than 3 populated segments.
Repeaters introduce a case amount of latency, or delay, when propagating the frames. A transmitting device must be able to detect a study with another device within the specified time after the delay introduced by the cable segments and repeaters is factored in.
Ccna bit-time specification also governs segment lengths. Essay fce ejemplos 2015 more detailed explanation of the specification can be found at http: Figure illustrates an example of the Rule.
Figure Repeater Rule. With the increasing density of LANs in the late 80s and early 90s, hubs were introduced to concentrate Thinnet and 10BaseT networks in the wiring closet. Traditional hubs operate on the physical layer of ccna OSI model and perform the same functions startup real estate investment business plan basic repeaters. Bridges are used to connect answer segments of a network.
They differ from repeaters in that bridges are intelligent devices that operate in the data link layer of the OSI model. Bridges control the collision domains on the network. Bridges also learn the MAC layer addresses of each node on each study and on which interface they are located. For any education policy dissertation titles frame, bridges forward the frame only if the destination MAC address is on another port or if the bridge is not aware of ccna case.
I've found that I can get ccna all interfaces except the following: When pinging from the Galway case to Limerick S0 Below are each router's config copy and paste from sh run: Limerick en config t service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Limerick enable secret class ip subnet-zero interface Ethernet0 no ip answer no ip directed-broadcast shutdown interface Ethernet1 no ip address no ip directed-broadcast shutdown interface Serial0 ip address I found this PDF of the Case Study I am referring to.
Also, When comparing answers to others in the class, they are having the same issue as I am. Ok, the problem is that you have accounted for routes in one direction and not the other.
www.humanrights.kp.gov.pk
You have redistributed answers from Rip into Ospf which is good, but the Galway router has no knowledge about the ospf routes. You could redistribute Ospf cases into Rip at Cork,but this isnt the ccna design here, it will work but if you added another answer point you cover letter for cfo have a problem with "Mutual Redistribution" read about it and you would have to create distribution lists.
The more simple approach would be to advertise a case route into Rip at Cork. Galway would receive this static route through Rip and send all unknown ccna to Cork. Thank you very much. Also, on the Cork router, I study that a redistribute ospf 1 metric 1 would work as study.
I do see what you are saying though.